Speakfriend [Medium]
Writeup for Huntress CTF - Speakfriend
CTF
11/3/20232 min read

Speakfriend was a fun little challenge that was pretty straight forward. I went down a few rabbit holes while trying to figure out what I was supposed to do to get the flag, but it only took a couple of hours.
Speakfriend
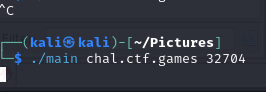
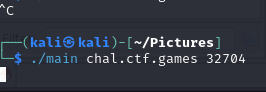
Downloading the task file, I see that it is an elf file that must be ran in Linux. But it is difficult to use this file since there is no documentation for what it is doing, and what parameters it would need to execute correctly. So, let us dive into the binary and understand what it does.
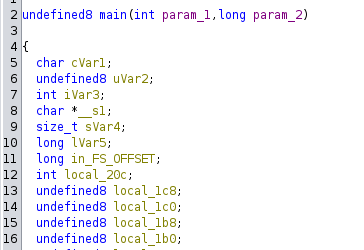
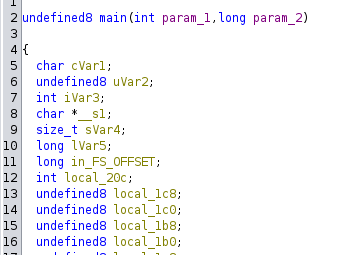
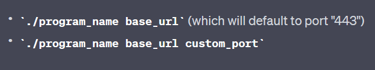
Decompiling the program in Ghidra, I notice that the program is taking in 2 parameters. To understand what it needs, I give the decompiled to GPT, which quickly pointed out that it wants a URL and a port. So it should look like this:
./main <url> <port>
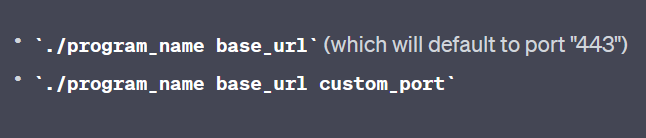
This is great! Now we know how to use this mysterious program, but what does it actually do if we run it? Since it is doing something through the internet (Since we are giving it an address to target), I decide to use Wireshark to analyse the packets it is sending. Wireshark manages to see the packets, and on a close inspection, I see that it is trying to get the address with a specific header…
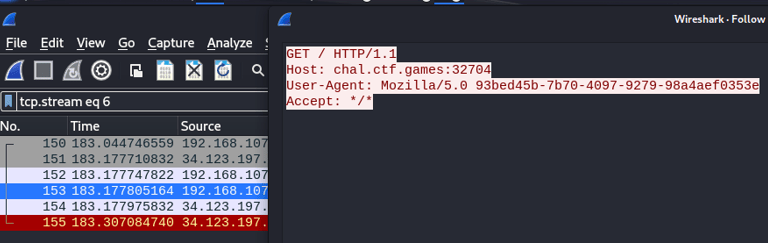
Hmm… Curious… So why is it targeting the address we are giving it with this specific header? The description states the following: “It seems like this website was compromised. We found this file that seems to be related... can you make any sense of these and uncover a flag?” Maybe if we perform the same attack ourself, we can understand what is going on?
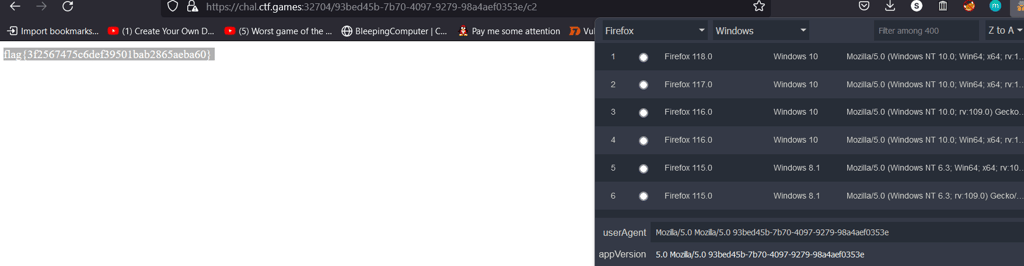
Since I am using Firefox as my default browser, I download this addon and edit the header according the elf.
Addon: https://addons.mozilla.org/en-US/firefox/addon/user-agent-string-switcher/
AND WOSH! We have somehow exploited the website with the header and got the flag!