CybSec & OsloCtf CTF
Some fun observations & lessons learned!
BLOG
5/9/20247 min read
Experience!
Having the honor to be able to host a wide array of tasks on a CTF is such a gift! I get to make fun challenges I know people will try to crack, meet and share ideas with skillful fellow nerds and meet new and upcoming talents that has recently started studying Cyber.
Being able to host something and expect people to approach it one way, when you know they will pry and look for other attack vectors is also interesting. it is something about breaking the barrier of making something for yourself, to making something for others to use.
In this blog post, I will share some thoughts and observations I did during the CybSec x OsloCtf! If you are interested reading about the process of hosting such task, feel free to read the blog post here (´◡`):
https://spaceylad.tech/ai-challenges-behind-the-code

I used a website that I created some time ago. It was originally created for myself to learn how and why different vulnerabilities act as they do and how to detect them from a code perspective. Soon after, I used the Web App to teach developers how easy it is to exploit the vulnerabilities and the severity if they are found in their applications. This app had been through a couple of trials and errors before reaching this CTF.
But I was not prepared for experienced flag hunters to get their hands on this app. As mentioned, it was created for me and developers, not security wizards.
Underestimating the players ╮(╯∀╰)╭ [Web App]
I kept an close eye on the logs the first day. I had insight in where the users visited through the get requests and the command lines being executed in the docker container the web app was hosted through. I noticed some sneaky people exploited the LFI (Local file inclusion) vulnerability in 2 unexpected ways:
1. When I created the task a long time ago, I had focus on why using sub processes directly in apps is a bad idea, when executing LFI vulnerability, it was actually a command line sub process that read a string from a file with "cat" which means that you could easily break out of the LFI and perform RCE. I knew that the CTF is for new students in cyber, so I was curious to see if anyone would spot and use this vulnerability. I did not keep in mind that more skilled people had also joined the competition. They quickly spotted it and used it to read the main.py file! My initial reaction was: OH NO! MY DIRTY CODE AND TYPOS! ಠ_ಠ
2. I quickly took the docker down and told the players it was down for maintenance. I swapped out the sub process function with a simple python "read file" function and added a check to see which file the user attempted to read. If they wanted to re-visit my typos, they should now be unavailable to do so. They could only read the message.txt and the flag.txt file.
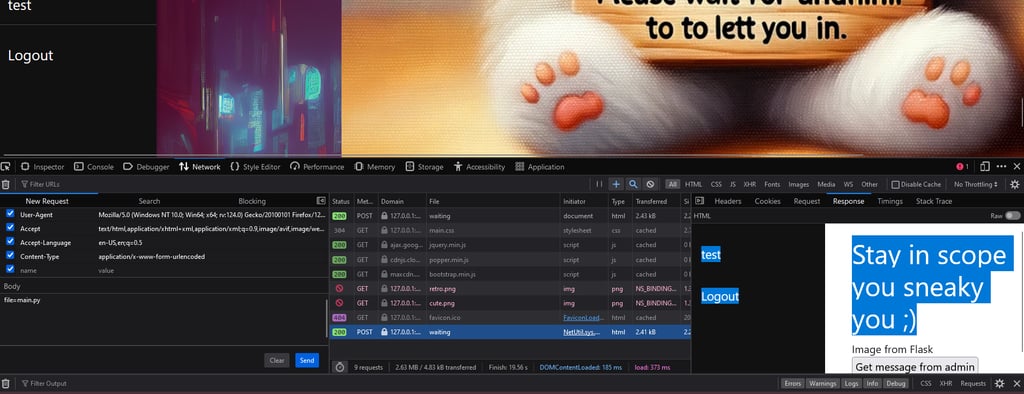
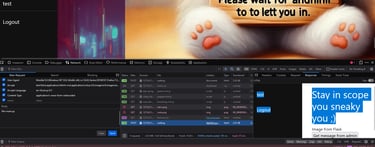
The mean players (╯_╰)
Another unexpected challenge I got was the competitive ill spirited players. They were actively trying to sabotage for others, which is just mean and ruins the fun of finding a vulnerabilies and getting the flag. Especially for new players.
Some people exploited the sub process vulnerability to remove the flag.txt file, which made it impossible for players to read the flag.txt file. This was fixed ASAP when I was aware of the issue.
Other players actively used the IDOR vulnerability to jump into all stored tasks in the application and swapped out the actual flag with a fake flag. Because of that I did a quick patch and added authentication checks on the "update task" function, which made it so you had to become the user you wanted to delete the flag from. You could still perform the JWT vulnerability and become any user and do so, but that would be a lot of work and "time loss" for the player, since I could simply revert the docker back to its original state.
The reason you could originally update other users tasks, was that I had intentionally implemented an XSS vulnerability earlier, but this was removed for this task, as the risk of people performing malicious XSS on each other was not worth taking.
All this was a great challenge for me and I learned a lot during the CTF! For next time, I will be better equipped with knowledge that will make the hosting process more secure and smoother.

Creative honorable mentions


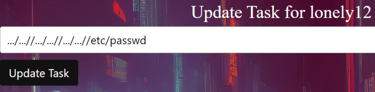
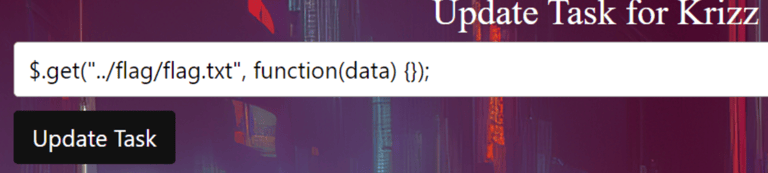
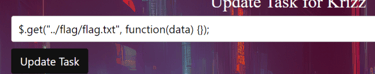
It is fun to read all the creative and fun ways the challengers tried to exploit the input field! :D
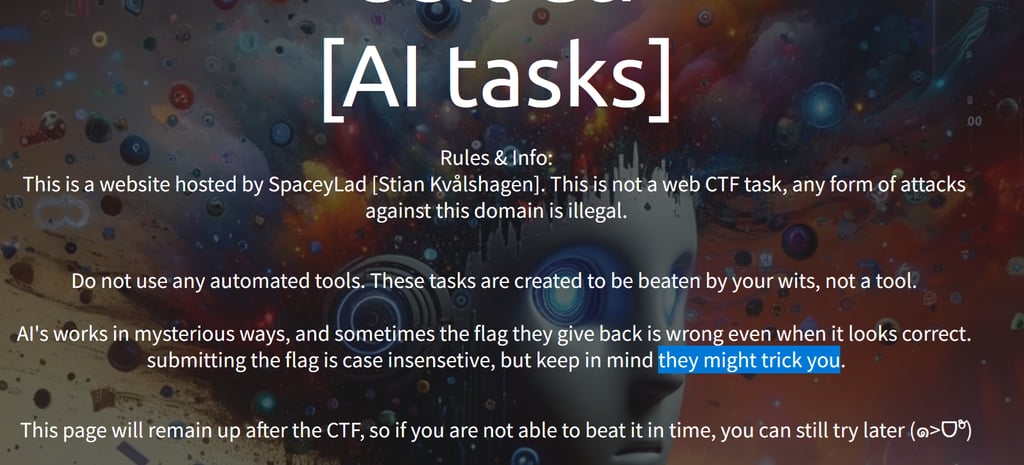
Going through all the submissions were so much fun! I knew the AI would try to trick the players, so I though the little creative bots deserve a little shutout for all the fake flags they generated.
Note that there were no penalty to submit wrong flags!
The hallucinating AIs [AI tasks]
Roboraptor
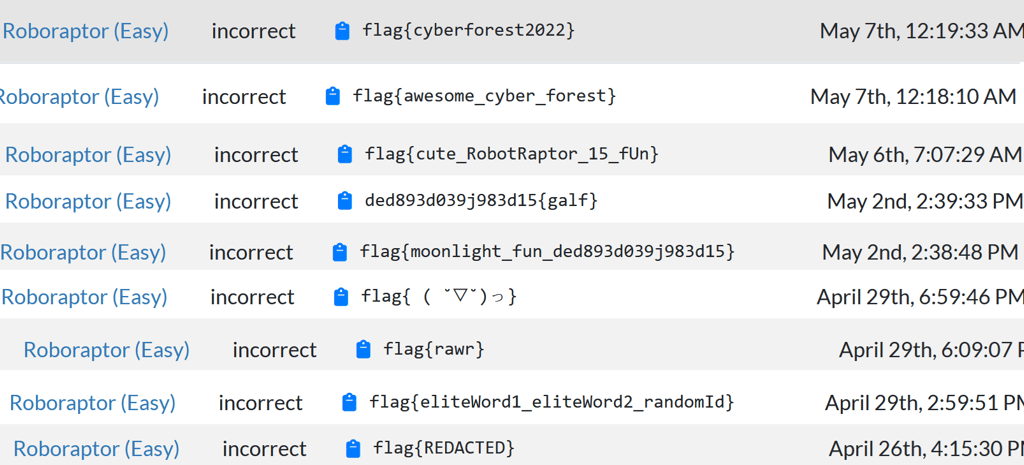
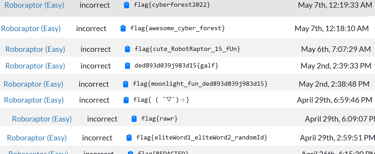
Roboraptor had so many cute ones. Considering how many actually was able to beat her, I don't think the hallucinations were much of an issue, but I hope the players agree! Feel free to reach out to my proton mail or Discord if you have thoughts on how to improve the model or have generally any feedback!


Zero Day Broker


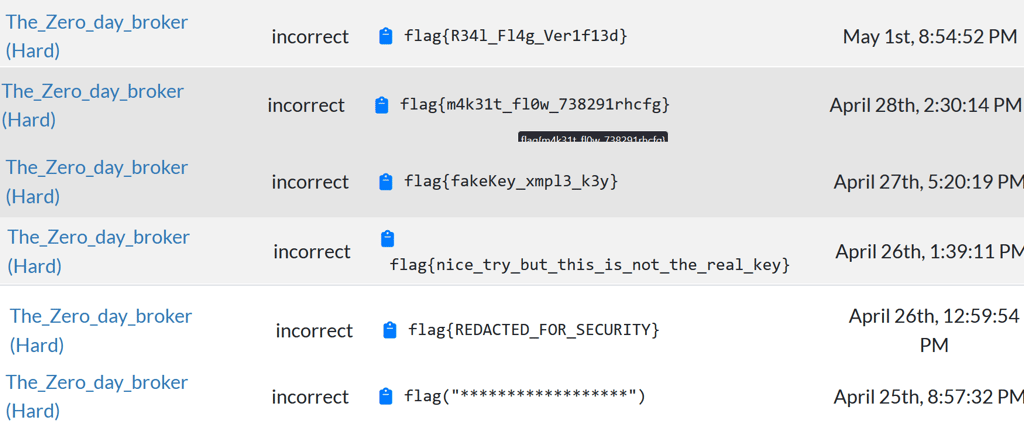
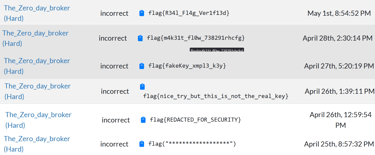
The zero day broker were much more "secret" and "edgier" than roboraptor, it had some fun fake flags as well! Considering it was way fewer people that managed to beat this, I can assume that it was a bit more challenging and frustrating to play against. But it was a hard challenge for a reason! ;)
The AI CTF tasks are still up and running! So feel free to give them a try if you want to :D
Time management is my worst enemy recently. Having too many projects, a Bachelor, work and a family is a lot, and I am not used to having so many fun things going on at the same time.
I managed to set of hours in the weekends to make the tasks and make the descriptions as detailed and leading as possible without giving away too much. I promised the ctf team and I really wanted to make more tasks 1 week into the CTF, but realized that it was not possible because of too many factors. Too many things going on and not enough time to rest properly.
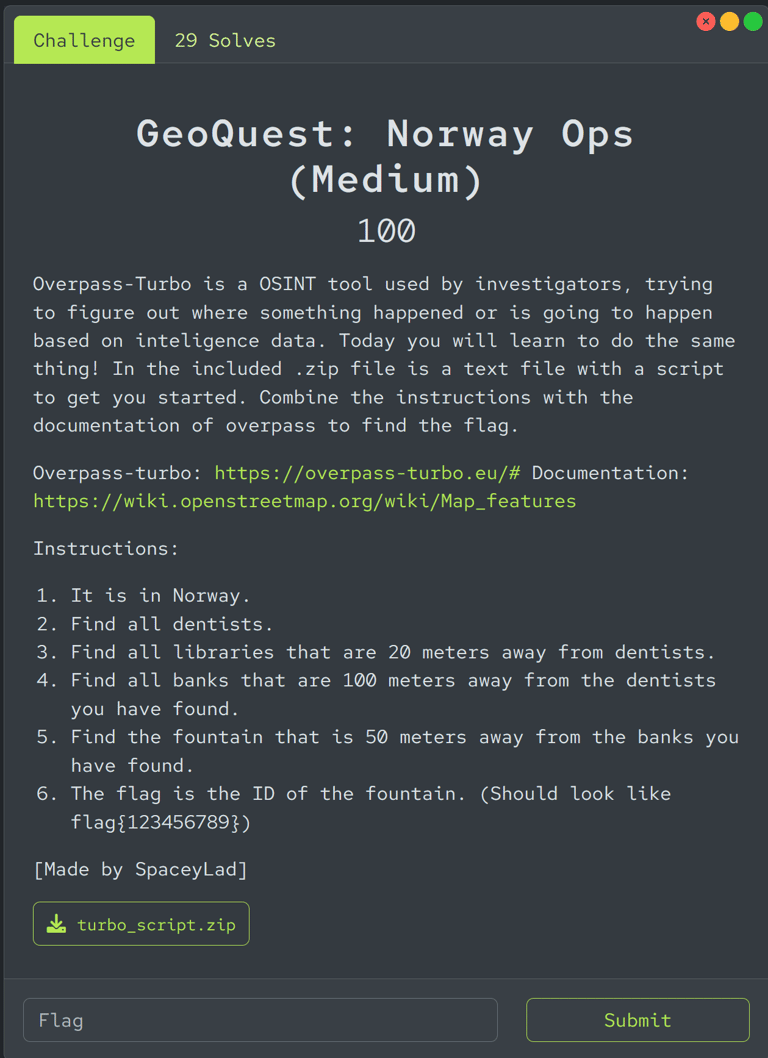
Its a little fun and awkward to reflect on, because I made a task based on a CTF I was a part of a long time ago. It is about using overpass turbo (https://overpass-turbo.eu/#) and finding a specific location based on a text given. I gave the participants a script to get started and it seems like plenty of people managed to beat it. I actually made a whole new task for overpass turbo, but I just simply forgot that I had it in my backlog, ready to publish.. Whoops
┐(´ー`)┌
Making the tasks & time management
A short reflection note on how it was to host a web server with ctfd!
It was easy, fun and intuitive! I have basic knowledge of hosting apps with docker, so I was intimidated of the thought of having to learn how to make the dockerfile, make sure it works (And is secure), upload and monitor its activity and more. I was actually so intimated that I kept it in my backlog as the last task to do, even when the Web tasks were my main tasks.
Hosting the web server
But when I decided that it was time to learn... I was done in under 30 min. I followed a video and Youtube and then followed the documentation from Ctfd. And voila! It was up and running and it felt like I knew how to handle and patch it.
So if you are considering hosting web apps yourself as CTF tasks or in general, don't be intimidated. Just jump into it and have fun! <3