BlackCat I [Medium]
Writeup for Huntress CTF - BlackCat I
CTF
11/2/20232 min read
BlackCat ransomware was a sneaky challenge. Because of how all the previous tasks was before this, I immediately thought this was a Reverse engineering task. But after running the code in Ghidra and dnSpy I quickly realized the fact that “No ransomware gang would actually hide their code inside their decryptor...” It just does not make any sense handing the file with the key to the victim if they need to get the key from the ransomware operator anyways. After realizing this, I quit the RE thought process and went back to the drawing board. (As a afterthought, I should have gone deeper and learned what kind of algorithm they were using to encrypt/decrypt files… But thankfully I figured that out with experience)
Reverse engineering
I started to analyse the files to look for any hints or patterns that could lead me to understand their algorithm better, and after looking at them for a while, I remembered something from my early University days... We learned about XOR and how it is possible to reverse the key if you have the original file. The clue that leads me in this direction was the file “Hamlet” by Shakespeare, since I have seen .txt files like this out in on the internet before, so I thought that if I find the original file... Then maybe I can reverse the key? While searching for the key, I could see that HuskyHacks also kept mentioning his adorable cats name on Discord “Cosmos” multiple times, something I took a mental note of.
Link to the original: https://www.gutenberg.org/files/1524/1524-0.txt
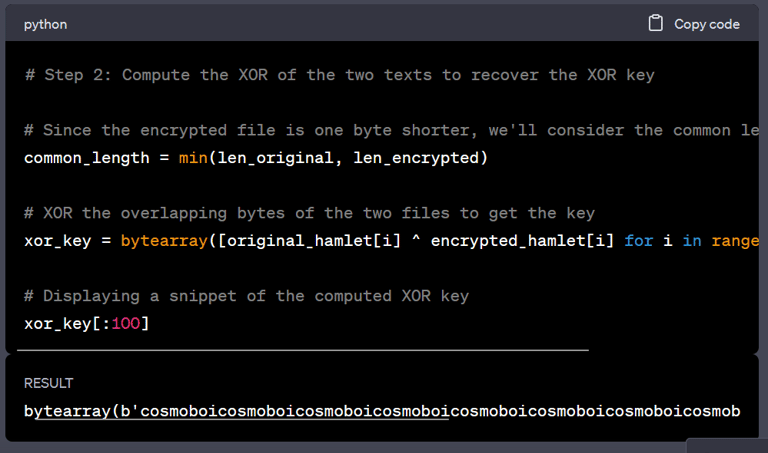
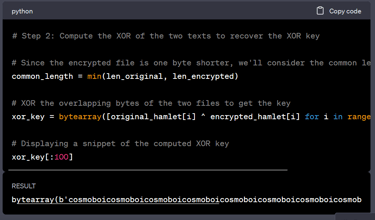
I managed to find the original file and asked GPT to make a XOR decryptor python script for me (Since I am lazy...). I made a local environment with the decryptor.py, hamlet.txt.encry and hamlet.txt, I ran the script and VOILA! We got the key: “cosmoboicosmoboicosmoboicosmoboicosmoboicosmoboicosmoboicosmoboicosmoboicosmoboicosmoboicosmoboicosm..”
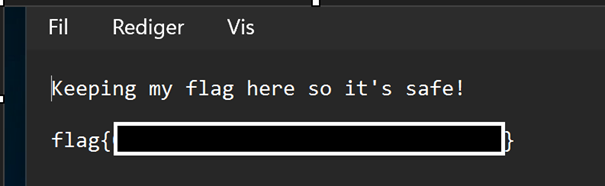
I put the key into the decryptor and BAM! All the files were decrypted! Including the flag.txt.